Security / Multi-Tenancy
Learn how to use multi-tenancy in Semaphor
Overview
Semaphor provides multiple options for securing and segmenting customer data based on tenant isolation. You can implement Connection-Level, Schema-Level, and Row/Column-Level security policies to control user access within your application.
Connection-Level Security
Connection-level security enables strict data isolation by assigning dedicated databases or data sources to each tenant. With connection-level policies, database connection strings and file paths can be dynamically parameterized based on the requesting tenant. This approach eliminates dashboard duplication and ensures secure data access.
How It Works
When a user authenticates into your app, Semaphor generates AuthToken based on the user's tenancy and profile. This token ensures access only to the authorized data.
For Files (Amazon S3)
In Semaphor, you can visualize .csv or .parquet files stored in Amazon S3. To achieve tenant-based isolation, configure a connection policy that dynamically adjusts the file path based on the tenant. A common pattern is folder-based segmentation:
You can create a connection policy using a tenant parameter. You can also have more than one parameter in the connection policy.
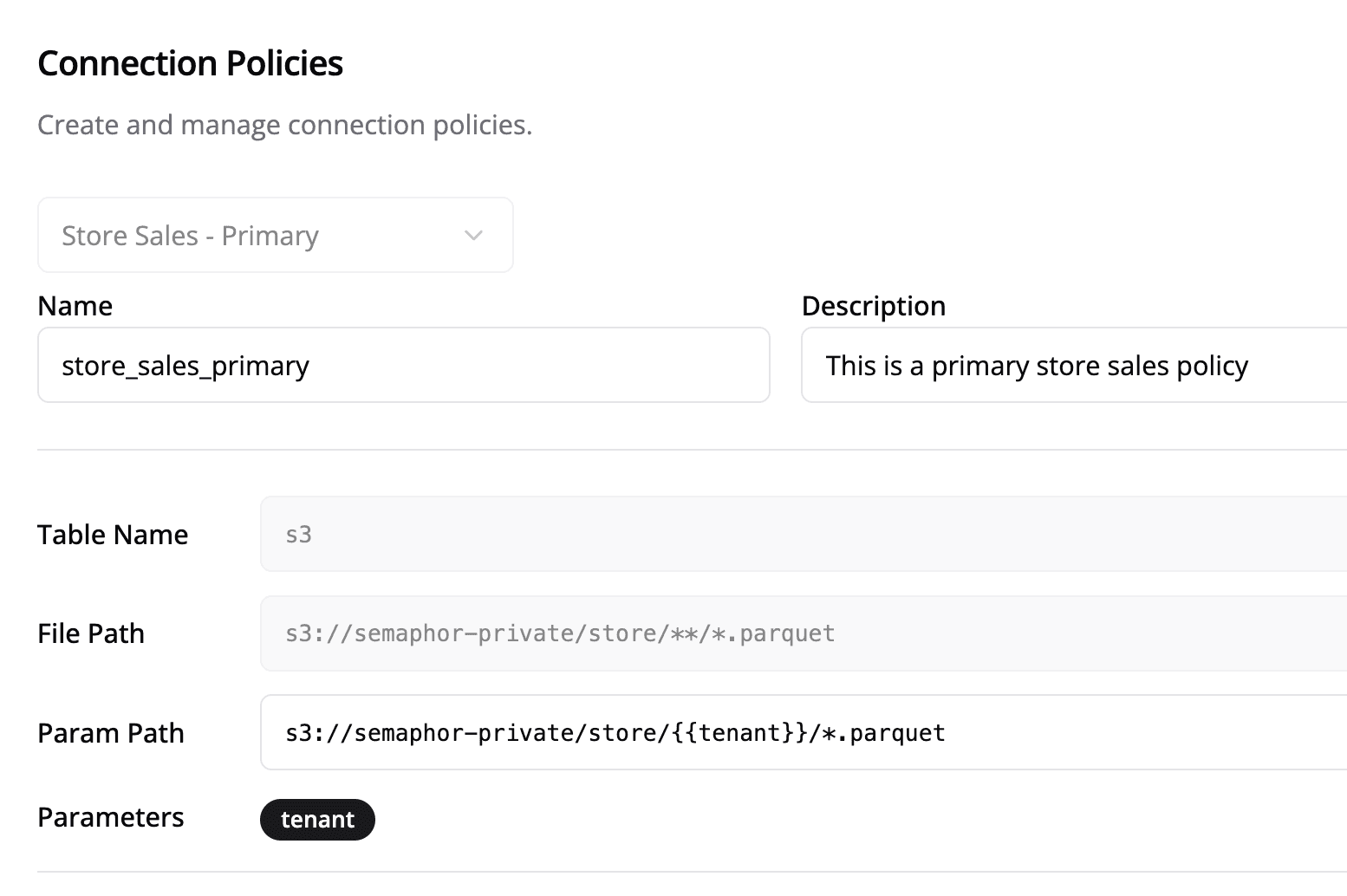
For Databases
Semaphor supports connections to SQL-compatible databases. A common approach for tenant-based isolation is to have separate databases per tenant:
The following connection policy parameterizes the database part of the connection string:
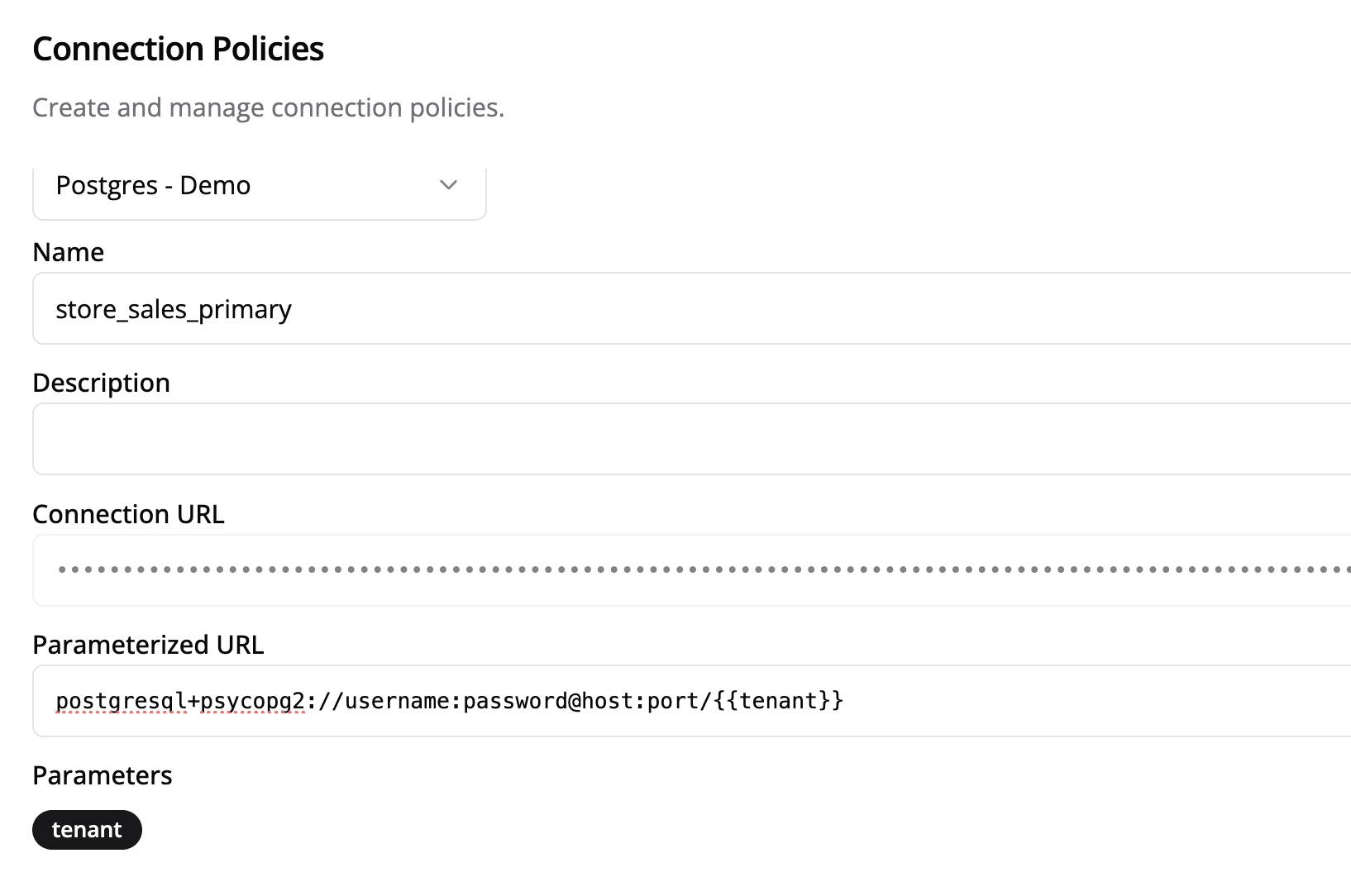
Applying Connection Policies
To apply a connection policy, construct a connection policy object and include it when requesting an authentication token:
Security Note
The token generation function must be run on the server side. Do not expose
DASHBOARD_SECRET in client-side code in production.
Schema-Level Security
Schema-level security provides a middle ground between connection-level and row/column-level security by isolating tenant data at the database schema level. This approach allows multiple tenants to share the same database instance while maintaining complete data isolation through dedicated schemas.
How It Works
When a user authenticates into your app, Semaphor uses the sls (Schema Level Security) parameter to automatically route users to their assigned schema. This ensures tenants can only access their designated schema while sharing the same database infrastructure.
Database Schema Structure
In a schema-level security model, each tenant gets their own dedicated database schema:
publicschema contains shared tables and internal data for your organization- Each tenant (like
tenant_a,tenant_b, etc.) gets a dedicated schema with tenant-specific tables - Table structures remain consistent across tenant schemas for easier maintenance
Applying Schema-Level Security
To apply schema-level security, include the sls parameter when requesting an authentication token:
Security Note
The token generation function must be run on the server side. Do not expose
DASHBOARD_SECRET in client-side code in production.
Benefits of Schema-Level Security
- Complete Data Isolation: Each tenant's data is physically separated in different schemas
- Shared Infrastructure: Multiple tenants can share the same database instance
- Consistent Structure: Table schemas remain consistent across tenants for easier maintenance
- Performance: No complex filtering logic required at the application level
- Scalability: Easy to add new tenants without infrastructure changes
Row/Column-Level Security
Row/Column-Level policies provide logical isolation when all customer data resides in a single database table or set of files. These policies function as hard filters, restricting access to specific rows or columns based on the tenant.
How It Works
When a user authenticates, Semaphor applies the defined security policy to the authentication token. This policy restricts access at the row and column level within the dataset.
Example Policy
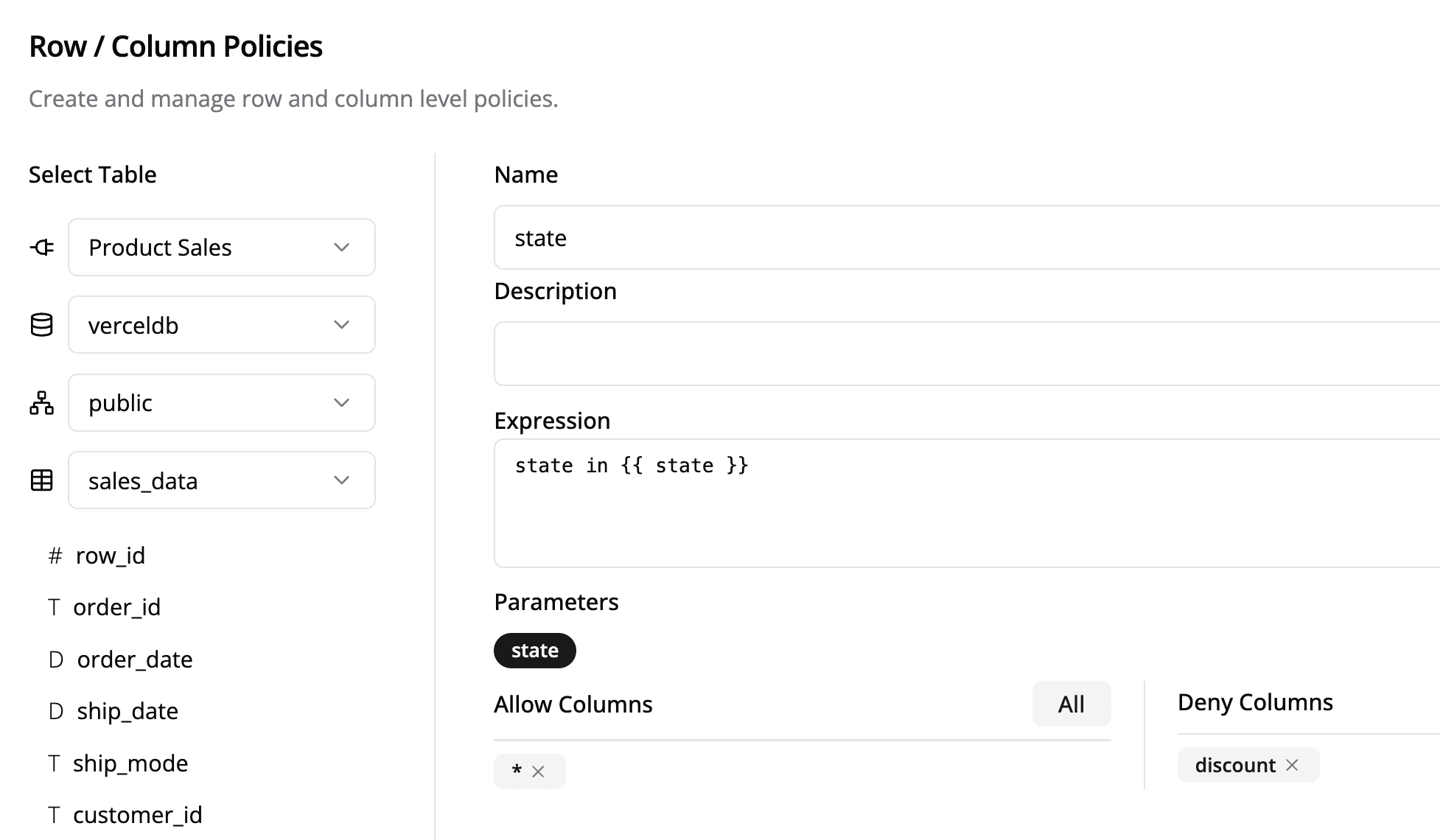
This Row-Level policy filters data based on a state parameter, ensuring users only see data relevant to them. Additionally, specific columns, such as discount, can be restricted from access.
Applying Row/Column-Level Policies
Security Note
The token generation function must be run on the server side. Do not expose
DASHBOARD_SECRET in client-side code in production.
Now whenever sales_data table is referenced in the Card SQL, this policy expands into the following SQL expression:
Combining Security Policies
You can use connection-level, schema-level, and row/column-level policies together for enhanced security, ensuring comprehensive data isolation and access control. This approach is ideal for multi-tenant architectures requiring flexible security configurations:
- Connection-Level + Schema-Level: Use dedicated databases with schema isolation for maximum security
- Schema-Level + Row/Column-Level: Combine schema isolation with fine-grained access control
- All Three: Implement the most comprehensive security model with physical and logical isolation
By implementing these security measures, you can effectively manage data access while maintaining a secure and scalable multi-tenant environment in Semaphor.